DVCTF 2025 - LouvreSecuritySystem [Hardware]
Difficulty : Easy
Team : Phreaks 2600
Topics : hardware, DVID, UART

TL;DR
- Connect to the UART port of the board with a baudrate of 9600 and log with “visitor:monalisa”
- Read welcome.txt and understand you have to log to “leonardo” account
- Recover the pw.txt file and grep ’leonardo'
- Try the 3 passwords possiblities and
- Once logged, get the MQTT channel
/var/log/security.log - Use the available MQTT commands :
mqtt --connectand thenmqtt --validate devices/0a56eecf-2955-4756-8f5d-80adc2e55ac0
Introduction
During the DaVinci CTF 24th May 2025, we participated with Phreaks 2600 at the on-cite competition of the CTF. There were 3 hardware challenges were we flagged 2 out of 3. Here’s the writeup of the easy one.
Challenge
The board
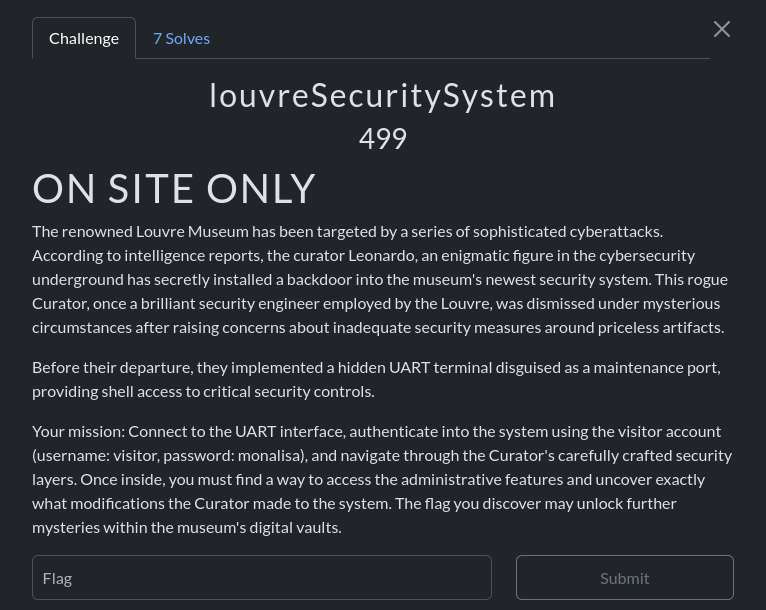
The challenge was hosted on a DVID v2 board and we were supposed to connect to the UART debug port.
This board need to get a power supply to work, so with the USB to TTL (UART to USB) we had to connect a wire from the 5V on it to the 5V on the board with jumper wires and plug the GND to any GND on the board and then the screen boot up.

On the screen we have got the correct baudrate (9600) to connect so we can directly use it with screen or minicom, tool to interact with serial ports:
|
|
And we can press the reset button on the board to get the initialisation screen :
UART restricted shell
|
|
We enter the logins given in the description : login visitor:monalisa:hJMQgiul
And the we get in a kind of linux shell :
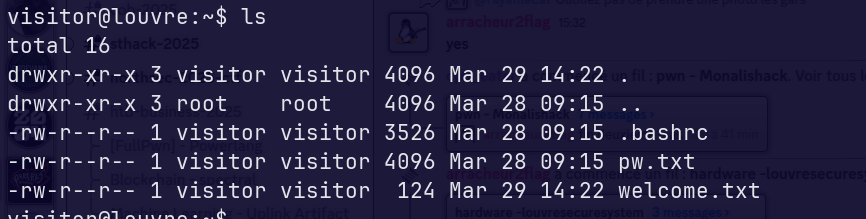
Reading the description I learnt that I had to “access administrative features” so I thought I had to privesc put trying sudo -l returned that the command was unknown. Typing help showed the available functions : logout, cat, ls .... So we were on a restricted shell.
Reading the welcome.txt we get this :
Welcome to the Louvre Museum Security System
For visitor inquiries, please contact the information desk.
For administrative access, please use the leonardo account
So we get to log to leonardo account, the only information we got is the file pw.txt.
There were 100 passwords in it so I had the idea to brute force it with python serial but it just didn’t work.
pw.txt
GlassPyramid235%HdimaryPssalG
VenusDeMilo625&BoliMeDsuneV
VenusDeMilo497&BoliMeDsuneV
RomanPortraiture856#HerutiartroPnamoR
VenusDeMilo268!JoliMeDsuneV
AncientEgypt213!JtpygEtneicnA
AncientEgypt933&C
MedievalWell625$DlleWlaveideM
EugeneDelacroix331$J
CycladicArt199&ItrAcidalcyC
GlassPyramid448%G
PaoloVeronese844!IesenoreVoloaP
MedievalWell882$AlleWlaveideM
JeanFrancoisChampollion706&F
CycladicArt250#B
JeanFrancoisChampollion831*AnoillopmahCsiocnarFnaeJ
RomanPortraiture589!EerutiartroPnamoR
WeddingAtCana979%JanaCtAgniddeW
RomanPortraiture525*JerutiartroPnamoR
TheodoreGericault161$A
JacquesLouisDavid622&EdivaDsiuoLseuqcaJ
WingedVictory243$A
VenusDeMilo992*ColiMeDsuneV
RomanPortraiture898&G
GreekAntiquities993@CseitiuqitnAkeerG
RomanPortraiture174#AerutiartroPnamoR
JacquesLouisDavid100@E
CoronationOfNapoleon484$D
VenusDeMilo326%C
WeddingAtCana660$DanaCtAgniddeW
CoronationOfNapoleon584&EnoelopaNfOnoitanoroC
EugeneDelacroix604!GxiorcaleDeneguE
Napoleon315$JnoelopaN
FrenchSculptures712&GserutplucShcnerF
WingedVictory977*CyrotciVdegniW
WeddingAtCana557#E
WeddingAtCana161!B
WingedVictory866!HyrotciVdegniW
LibertyLeadingThePeople263#IelpoePehTgnidaeLytrebiL
WeddingAtCana529@EanaCtAgniddeW
RomanPortraiture506*J
AncientEgypt655$ItpygEtneicnA
EugeneDelacroix899@D
MedievalWell358$D
JacquesLouisDavid906%IdivaDsiuoLseuqcaJ
RomanPortraiture813@C
PaoloVeronese870#B
FrenchSculptures511%FserutplucShcnerF
Napoleon152$C
CycladicArt618!AtrAcidalcyC
EugeneDelacroix434!G
TheodoreGericault239!D
GlassPyramid707@DdimaryPssalG
LeonardoDaVinci488#BicniVaDodranoeL
FrenchSculptures583$HserutplucShcnerF
RaftOfTheMedusa898*F
LeonardoDaVinci743$BicniVaDodranoeL
IslamicArt396#A
TheodoreGericault353@AtluacireGerodoehT
GreekAntiquities161%AseitiuqitnAkeerG
PaoloVeronese303#DesenoreVoloaP
PaoloVeronese621%I
WingedVictory982&ByrotciVdegniW
WeddingAtCana144#I
RomanPortraiture518*D
AncientEgypt563&J
CoronationOfNapoleon369%G
AncientEgypt414*B
CoronationOfNapoleon764@DnoelopaNfOnoitanoroC
CycladicArt811&DtrAcidalcyC
GrandGallery835@ByrellaGdnarG
JacquesLouisDavid462#D
Napoleon409!GnoelopaN
RomanPortraiture895&A
EugeneDelacroix354@FxiorcaleDeneguE
MedievalWell160$D
GrandGallery547$A
RomanPortraiture296%BerutiartroPnamoR
FrenchSculptures874@BserutplucShcnerF
Napoleon616*G
VenusDeMilo153%C
CoronationOfNapoleon647#J
PaoloVeronese606&H
RaftOfTheMedusa216&D
MedievalWell892@I
CoronationOfNapoleon880@I
WeddingAtCana215!C
EugeneDelacroix828$JxiorcaleDeneguE
CoronationOfNapoleon916@E
MonaLisa457#GasiLanoM
LeonardoDaVinci905@JicniVaDodranoeL
GlassPyramid141%EdimaryPssalG
GreekAntiquities244@I
RaftOfTheMedusa736&C
TheodoreGericault312&B
TheodoreGericault349#AtluacireGerodoehT
IslamicArt196$J
EugeneDelacroix671*BxiorcaleDeneguE
JeanFrancoisChampollion367%JnoillopmahCsiocnarFnaeJ
GlassPyramid474&H
But as I’m smart, I grep’d “leonardo” on the file and got three matches :
LeonardoDaVinci488#BicniVaDodranoeL
LeonardoDaVinci743$BicniVaDodranoeL
LeonardoDaVinci905@JicniVaDodranoeL
It ended that LeonardoDaVinci743$BicniVaDodranoeL was the correct password with the login leonardo.
UART shell with admin features
Here are the files :
|
|
And in help we got interesting commands :
mqtt --connect
mqtt --validate <device>
mqtt --status
In the security.log we learn about an MQTT device.
|
|
We get the MQTT device ID.
Running mqtt --status we learn that it isn’t connect. So I connect it with mqtt --connect
And then I can use mqtt --connect devices/0a56eecf-2955-4756-8f5d-80adc2e55ac0 :
|
|